SCF - Make Compliance A Natural Byproduct of Secure Practices
What is the Secure Controls Framework (SCF)? To answer this question, we have provided a short video to answer some of the most common questions we receive. In addition, we highly encourage everyone to read the SCF Overview and Instructions - https://content.securecontrolsframework.com/SCF-Recommended-Practices.pdf.
The SCF is a more efficient way to operationalize cybersecurity and data privacy operations by simplifying the underlying controls that power an organization’s cybersecurity program. The reality is that most organizations struggle with defining the minimum security requirements that are necessary to address both their compliance obligations and needs for secure practices. The SCF provides a straightforward and scalable method to define those “must have” and “nice to have” requirements into a holistic control set to operationalize cybersecurity operations, risk management and third-party governance. There is no cost to use the SCF and quite a few Governance Risk and Compliance (GRC) platforms natively support the SCF as a built-in control set.
In simple terms, the SCF is a metaframework where it is a catalog of controls made up of over 100 cybersecurity and data privacy laws, regulations and frameworks. This control catalog contains roughly 1,200 controls and is logically organized into 33 domains. The structure of the SCF normalizes disparate control language into something that is usable across technology, cybersecurity, privacy and other departments where they can share the same control language. The SCF enables not only intra-organization standardization, but inter-organization standardization where control GOV-03 means the same thing to one organization to any other organization using the SCF. That is truly unique to the SCF.
The SCF is made up of volunteers who are specialists within the cybersecurity profession who have a focus on Governance, Risk and Compliance (GRC) and the cybersecurity side of data privacy. These are auditors, engineers, architects, incident responders, consultants and other specialists who live and breathe these topics on a daily basis. The end product is "expert-derived content" that makes up the SCF.
More Than Just A Control Set
The SCF is much more than just a control set!
- Each control has a control weighting to help understand risk, since not all controls are the same.
- There is a built-in risk catalog and threat catalog, where those risks and threats are mapped to SCF controls.
- There is a capability maturity model to help define what right looks like for your organization.
- There is a risk management model to enable holistic risk management practices at the control level.
- There is an evidence request list to define expected assessment artifacts that would be reasonably expected to satisfy controls.
- We even have assessment objectives to help provide objective criteria that can be used to assess controls.
The sweet spot for the SCF is medium to large organizations, but it has been successfully used by small organizations. Any organization with complex compliance requirements can benefit from using the SCF. We are just trying to make it easier for cybersecurity practitioners to do their jobs, since we all benefit from organizations having better security practices in place.
SCF Is Built To Fix A Broken Industry
Like it or not, cybersecurity is a protracted war on an asymmetric battlefield - the threats are everywhere and as defenders we have to make the effort to work together to help improve cybersecurity and data privacy practices, since we all suffer when massive data breaches occur or when cyber attacks have physical impacts.
The SCF was created to help organizations do better with their cybersecurity practices. Hackers share information on attack methods with other hackers, so why shouldn’t the good guys share information on how to best protect an organization? We decided to take action and make a difference, since we feel it is too important to wait for someone else to fix the problems that exist. The SCF went live in 2018 and its adoption is now worldwide, where it is in use by some of the biggest corporations and governments.

We provide cybersecurity and data privacy control guidance to cover the strategic, operational and tactical needs of organizations, regardless of their size, industry or country of origin. The end state is to help organizations not only become and stay compliant, but maintain secure operations.
The SCF Council has a few humble goals:
- From a framework perspective, become the leading metaframework that organizations can use as a "Rosetta Stone" to build secure and compliant cybersecurity and data privacy programs; and
- From a process improvement perspective, leverage the SCF's Conformity Assessment Program (CAP) to fundamentally disrupt/reform how cybersecurity third-party assessments are performed.
 |
The Secure Controls Framework™ (SCF) focuses on internal controls. These are the cybersecurity and privacy-related policies, standards, procedures, technologies and associated processes that are designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented, detected and corrected. This page will covers the following topics:
For your off-line reading pleasure, you can download the PDF version of this helpful information |
The Secure Controls Framework™ (SCF) Is The Common Controls Framework™ (CCF)
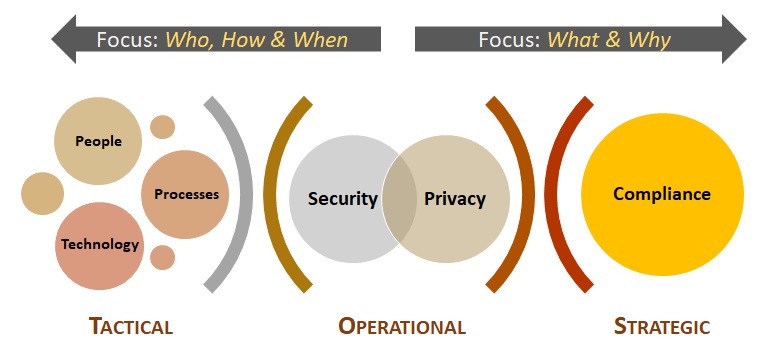
The SCF is a "Rosetta Stone" approach to cybersecurity and privacy controls, which makes it the Common Controls Framework™. The concept of the SCF is to have a metaframework (e.g., framework of frameworks) that is capable of addressing the broader People, Processes, Technology and Data (PPTD) that are what controls fundamentally exists to govern. The SCF can be used to assist with strategic planning down to tactical needs that impact the people, processes and technologies directly impacting your organization.
 |
Using the SCF should be viewed as a long-term tool to not only help with compliance-related efforts but to ensure security and privacy principles are properly designed, implemented and maintained. The SCF helps implement a holistic approach to protecting the Confidentiality, Integrity, Availability and Safety (CIAS) of your data, systems, applications and other processes. Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements. The approach looks at the following spheres of influence to identify applicable controls:
It is best to visualize the SCF as a buffet of cybersecurity and privacy controls, where there is a selection of 1,000+ controls available to you. Once you know what is applicable to you, you can generate a customized control set that gives you the controls you need to address your statutory, regulatory and contractual obligations. |
Why You Should Use The SCF
There is no sales pitch for using the SCF – the SCF is a free resource, so there is no financial incentive for us to make companies use it:
- For companies that have just one 1-2 compliance requirements, the SCF might be considered overkill for your needs.
- For companies that have 3+ compliance requirements (e.g., organization that has requirements to address ISO 27002, SOC 2, PCI DSS and GDPR), then the SCF is a great tool to streamline the management of cybersecurity and privacy controls.
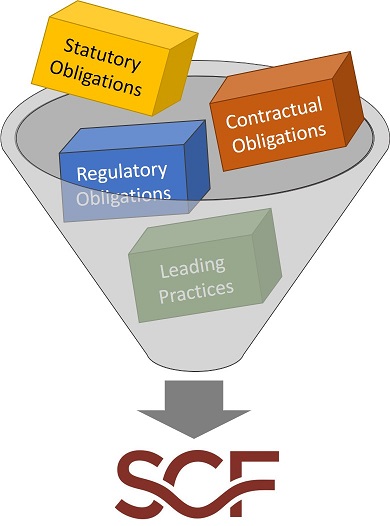
In developing the SCF, we identified and analyzed over 100 statutory, regulatory and contractual frameworks. Through analyzing these thousands of legal, regulatory and framework requirements, we identified commonalities and this allows several thousand unique controls to be addressed by the controls that makeup the SCF. For instance, a requirement to maintain strong passwords is not unique, since it is required by dozens of laws, regulations and frameworks. This allows one well-worded SCF control to address multiple requirements. This focus on simplicity and sustainability is key to the SCF, since it can enable various teams to speak the same controls language, even though they may have entirely different statutory, regulatory or contractual obligations that they are working towards.
The SCF targets silos, since siloed practices within any organization are inefficient and can lead to poor security, due to poor communications and incorrect assumptions.
What The SCF Is
The SCF is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems and applications. The SCF addresses both cybersecurity and privacy, so that these principles are designed to be “baked in” at the strategic, operational and tactical levels.
The SCF is:
- A control set.
- A useful tool to provide a “Rosetta Stone” approach to organizing cybersecurity and privacy controls so that the same controls can be used among companies and teams (e.g., privacy, cybersecurity, IT, project, procurement, etc.).
- Free for businesses to use. A result of a volunteer-led effort that uses “expert derived assessments” to perform the mapping from the controls to applicable laws, regulations and other frameworks.
The SCF also contains helpful guidance on possible tools and solutions to address controls. Additionally, it contains maturity criteria that can help an organization plan for and evaluate controls, based on a target maturity level.
What The SCF Is Not
While the SCF is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems and applications, the SCF will only ever be a control set and is not a “magic bullet” technology solution to address every possible cybersecurity and privacy compliance obligation that an organization faces.
The SCF is not:
- A substitute for performing due diligence and due care steps to understand your specific compliance needs.
- A complete technology or documentation solution to address all your security & privacy needs (e.g., the policies, standards, procedures and processes you need to have in place to be secure and compliant).
- Infallible or guaranteed to meet every compliance requirement your organization offers, since the controls are mapped based on expert-derived assessments to provide the control crosswalking that relies on human expertise and that is not infallible.
Common Controls Framework - Structured To Address Your Cybersecurity & Privacy Needs
The SCF contains over 1,000 controls that are organized into 33 domains (as shown below) to create a "best in class" approach to structuring the controls in a logical arrangement. Having a user friendly and logical taxonomy is important, since it helps discussing controls easier when there is a logical approach to both the naming and structure. The not only benefits internal teams (e.g., cyber, IT, privacy, procurement, legal, etc.) but it is designed to be used inter-organizationally, where GOV-03 means the same thing to your company as it does to other organizations that leverage the SCF. That is a big deal!
| # | Icon | SCF Domain | SCF Identifier | Cybersecurity & Data Privacy by Design (C|P) Principles |
| 1 | Cybersecurity & Data Privacy Governance | GOV | Execute a documented, risk-based program that supports business objectives while encompassing appropriate cybersecurity and data privacy principles that addresses applicable statutory, regulatory and contractual obligations. | |
| 2 | |
Artificial and Autonomous Technology | AAT | Ensure trustworthy and resilient Artificial Intelligence (AI) and autonomous technologies to achieve a beneficial impact by informing, advising or simplifying tasks, while minimizing emergent properties or unintended consequences. |
| 3 | |
Asset Management | AST | Manage all technology assets from purchase through disposition, both physical and virtual, to ensure secured use, regardless of the asset’s location. |
| 4 | |
Business Continuity & Disaster Recovery | BCD | Maintain a resilient capability to sustain business-critical functions while successfully responding to and recovering from incidents through well-documented and exercised processes. |
| 5 | |
Capacity & Performance Planning | CAP | Govern the current and future capacities and performance of technology assets. |
| 6 | Change Management | CHG | Manage change in a sustainable and ongoing manner that involves active participation from both technology and business stakeholders to ensure that only authorized changes occur. | |
| 7 | Cloud Security | CLD | Govern cloud instances as an extension of on-premise technologies with equal or greater security protections than the organization’s own internal cybersecurity and privacy controls. | |
| 8 | |
Compliance | CPL | Oversee the execution of cybersecurity and privacy controls to ensure appropriate evidence required due care and due diligence exists to meet compliance with applicable statutory, regulatory and contractual obligations. |
| 9 | |
Configuration Management | CFG | Enforce secure configurations for systems, applications and services according to vendor-recommended and industry-recognized secure practices. |
| 10 | |
Continuous Monitoring | MON | Maintain situational awareness of security-related events through the centralized collection and analysis of event logs from systems, applications and services. |
| 11 | |
Cryptographic Protections | CRY | Utilize appropriate cryptographic solutions and industry-recognized key management practices to protect the confidentiality and integrity of sensitive/regulated data both at rest and in transit. |
| 12 | |
Data Classification & Handling | DCH | Enforce a standardized data classification methodology to objectively determine the sensitivity and criticality of all data and technology assets so that proper handling and disposal requirements can be followed. |
| 13 | |
Embedded Technology | EMB | Provide additional scrutiny to reduce the risks associated with embedded technology, based on the potential damages posed from malicious use of the technology. |
| 14 | |
Endpoint Security | END | Harden endpoint devices to protect against reasonable threats to those devices and the data those devices store, transmit and process. |
| 15 | |
Human Resources Security | HRS | Execute sound hiring practices and ongoing personnel management to cultivate a cybersecurity and privacy-minded workforce. |
| 16 | |
Identification & Authentication | IAC | Enforce the concept of “least privilege” consistently across all systems, applications and services for individual, group and service accounts through a documented and standardized Identity and Access Management (IAM) capability. |
| 17 | |
Incident Response | IRO | Maintain a viable incident response capability that trains personnel on how to recognize and report suspicious activities so that trained incident responders can take the appropriate steps to handle incidents, in accordance with a documented Incident Response Plan (IRP). |
| 18 | |
Information Assurance | IAO | Execute an impartial assessment process to validate the existence and functionality of appropriate cybersecurity and privacy controls, prior to a system, application or service being used in a production environment. |
| 19 | |
Maintenance | MNT | Proactively maintain technology assets, according to current vendor recommendations for configurations and updates, including those supported or hosted by third-parties. |
| 20 | |
Mobile Device Management | MDM | Implement measures to restrict mobile device connectivity with critical infrastructure and sensitive/regulated data that limit the attack surface and potential data exposure from mobile device usage. |
| 21 | |
Network Security | NET | Architect and implement a secure and resilient defense-in-depth methodology that enforces the concept of “least functionality” through restricting network access to systems, applications and services. |
| 22 | |
Physical & Environmental Security | PES | Protect physical environments through layers of physical security and environmental controls that work together to protect both physical and digital assets from theft and damage. |
| 23 | |
Data Privacy | PRI | Align data privacy practices with industry-recognized data privacy principles to implement appropriate administrative, technical and physical controls to protect regulated personal data throughout the lifecycle of systems, applications and services. |
| 24 | Project & Resource Management | PRM | Operationalize a viable strategy to achieve cybersecurity & privacy objectives that establishes cybersecurity as a key stakeholder within project management practices to ensure the delivery of resilient and secure solutions. | |
| 25 | |
Risk Management | RSK | Proactively identify, assess, prioritize and remediate risk through alignment with industry-recognized risk management principles to ensure risk decisions adhere to the organization's risk threshold. |
| 26 | |
Secure Engineering & Architecture | SEA | Utilize industry-recognized secure engineering and architecture principles to deliver secure and resilient systems, applications and services. |
| 27 | Security Operations | OPS | Execute the delivery of cybersecurity and privacy operations to provide quality services and secure systems, applications and services that meet the organization's business needs. | |
| 28 | |
Security Awareness & Training | SAT | Foster a cybersecurity and privacy-minded workforce through ongoing user education about evolving threats, compliance obligations and secure workplace practices. |
| 29 | |
Technology Development & Acquisition | TDA | Develop and test systems, applications or services according to a Secure Software Development Framework (SSDF) to reduce the potential impact of undetected or unaddressed vulnerabilities and design weaknesses. |
| 30 | |
Third-Party Management | TPM | Execute Supply Chain Risk Management (SCRM) practices so that only trustworthy third-parties are used for products and/or service delivery. |
| 31 | |
Threat Management | THR | Proactively identify and assess technology-related threats, to both assets and business processes, to determine the applicable risk and necessary corrective action. |
| 32 | Vulnerability & Patch Management | VPM | Leverage industry-recognized Attack Surface Management (ASM) practices to strengthen the security and resilience systems, applications and services against evolving and sophisticated attack vectors. | |
| 33 | |
Web Security | WEB | Ensure the security and resilience of Internet-facing technologies through secure configuration management practices and monitoring for anomalous activity. |
Integrated Controls Management (ICM) Approach To Building A Security Program
Building a security program that routinely incorporates security and privacy practices into daily operations requires a mastery of the basics. A useful analogy is with the children's toy, LEGO®. With LEGO® you can build nearly anything you want — either through following directions or using your own creativity. However, it first requires an understanding of how various LEGO® shapes either snap together or are incompatible.
Once you master the fundamentals with LEGO®, it is easy to keep building and become immensely creative since you know how everything interacts. However, when the fundamentals are ignored, the LEGO® structure will be weak and include systemic flaws. Security and privacy really are not much different, since those disciplines are made up of numerous building blocks that all come together to build secure systems and processes. The lack of critical building blocks will lead to insecure and poorly architected solutions.
When you envision each component that makes up a security or privacy “best practice” is a LEGO® block, it is possible to conceptualize how certain requirements are the foundation that form the basis for others components to attach to. Only when the all the building blocks come together and take shape do you get a functional security / privacy program!
Think of the SCF as a toolkit for you to build out your overall security program domain-by-domain so that cybersecurity and privacy principles are designed, implemented and managed by default!
Controls Are Key To Everything In Cybersecurity & Data Protection
The premise of Integrated Controls Management (ICM) is that controls are central to cybersecurity and privacy operations, as well as the overall business rhythm of an organization.
ICM is designed to proactively address the strategic, operational and tactical nature of operating an organization’s cybersecurity and privacy program at the control level. ICM is designed to address both internal controls, as well as the broader concept of Supply Chain Risk Management (SCRM).
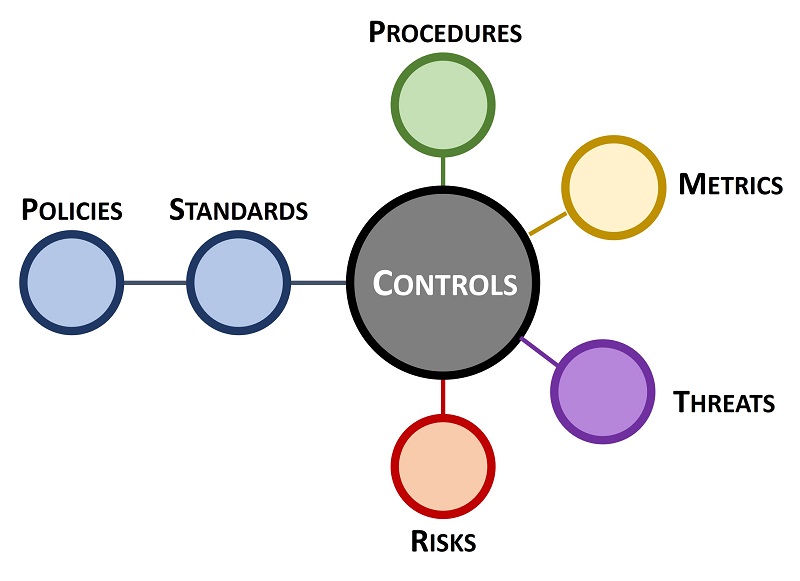 |
 |
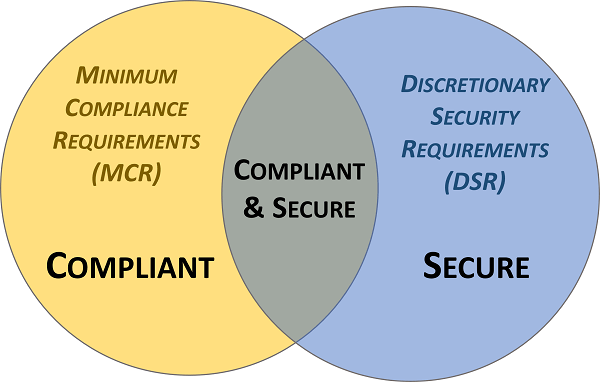
ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, an organization’s applicable controls are categorized according to “must have” vs “nice to have” requirements:
- Minimum Compliance Requirements (MCR) are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts. MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- Discretionary Security Requirements (DSR) are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments. DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
Using The SCF Starts With Defining "Must Have" & "Nice to Have" Requirements
As described above, the concept of MCR & DSR are a crucial step to get right, otherwise you will likely design it incorrectly that will leave gaps that can expose your organization to issues of non-compliance and/or inadequate security practices.
When you add MCR & DSR, you are able to define "what right looks like" for your organization, which equates to your Minimum Security Requirements (MSR) that can be published to project teams, risk management, engineers, etc. The MSR is the blueprint for an organization to build security and privacy in by design across the SDLC and business-as-usual operations.
Plan, Do, Check & Act (PDCA) Approach To Cybersecurity & Data Protection
Within the ICM, its principles are overlaid onto the following graphic to show how a PDCA approach for continuous improvement of your cybersecurity and data protection program is possible:
- Establish Context
- Define Applicable Controls
- Assign Maturity-Based Criteria
- Publish Policies, Standards & Procedures
- Assign Stakeholder Accountability
- Maintain Situational Awareness
- Manage Risk
- Evolve Processes
More Than Just A Control Set
Where the SCF sets itself apart from other metaframeworks is the following:
- Capability maturity criteria for each control
- Proposed control weighting (not all controls are as important in risk management decisions)
- Built-in risk catalog
- Built-in threat catalog
For the capability maturity criteria, we published the Cybersecurity & Data Privacy Capability Maturity Model (C|P-CMM).
To make use of the risk & threat catalogs, we published the Cybersecurity & Data Privacy Risk Management Model (C|P-RMM).
This is where the Integrated Controls Management (ICM) model ties all those capabilities together to help you design the controls that are right for your organization, as well as be able to leverage that same control set to help understand risks and threats. This is a "paint by numbers" approach to operationalizing your cybersecurity and data protection program!
Understanding Cybersecurity & Privacy By Design
Security by Design (SbD)
 |
These requirements come from numerous sources. In this context, some of the most important cybersecurity frameworks are:
|
Privacy by Design (PbD)
 |
These requirements come from numerous sources. In this context, some of the most important privacy frameworks are:
|
Statutory Cybersecurity & Privacy Requirements
Statutory obligations are required by law and refer to current laws that were passed by a state or federal government. From a cybersecurity and privacy perspective, statutory compliance requirements include:
-
US - Federal Laws
- Children's Online Privacy Protection Act (COPPA)
- Fair and Accurate Credit Transactions Act (FACTA) - including "Red Flags" rule
- Family Education Rights and Privacy Act (FERPA)
- Federal Information Security Management Act (FISMA)
- Federal Trade Commission (FTC) Act
- Gramm-Leach-Bliley Act (GLBA)
- Health Insurance Portability and Accountability Act (HIPAA)
- Sarbanes-Oxley Act (SOX)
-
US - State Laws
- California SB1386
- California Consumer Privacy Act (CCPA)
- Massachusetts 201 CMR 17.00
- Oregon ORS 646A.622
-
International Laws
- Canada - Personal Information Protection and Electronic Documents Act (PIPEDA)
- UK - Data Protection Act (DPA)
- Other countries' variations of Personal Data Protect Acts (PDPA)
Regulatory Cybersecurity & Privacy Requirements
Regulatory obligations are required by law, but are different from statutory requirements in that these requirements refer to rules issued by a regulating body that is appointed by a state or federal government. These are legal requirements through proxy, where the regulating body is the source of the requirement. It is important to keep in mind that regulatory requirements tend to change more often than statutory requirements. From a cybersecurity and privacy perspective, regulatory compliance examples include:
-
US Regulations
- Defense Federal Acquisition Regulation Supplement (DFARS) - NIST 800-171
- Federal Acquisition Regulation (FAR)
- Federal Risk and Authorization Management Program (FedRAMP)
- DoD Information Assurance Risk Management Framework (DIARMF)
- National Industrial Security Program Operating Manual (NISPOM)
- New York Department of Financial Services (NY DFS) 23 NYCRR 500
-
International Regulations
- European Union General Data Protection Regulation (EU GDPR)
- EU ePrivacy Directive
Contractual Cybersecurity & Privacy Requirements
Contractual obligations are required by legal contract between private parties. This may be as simple as a cybersecurity or privacy addendum in a vendor contract that calls out unique requirements. It also includes broader requirements from an industry association that membership brings certain obligations. From a cybersecurity and privacy perspective, common contractual compliance requirements include:
- Payment Card Industry Data Security Standard (PCI DSS)
- Financial Industry Regulatory Authority (FINRA)
- Service Organization Control (SOC)
- Generally Accepted Privacy Principles (GAPP)
Industry-Leading "Best Practices" for Cybersecurity & Privacy
Leading practices may be required under a contractual obligation with a client or partner, but these industry frameworks are commonly referenced for “what right looks like” with how technology is implemented. Leading frameworks generally more technical in nature and provide granular requirements. From a cybersecurity and privacy perspective, common leading frameworks include:
-
Cybersecurity Frameworks
- Center for Internet Security (CIS) Critical Security Controls (CSC)
- Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
- Department of Defense Cybersecurity Agency (DISA) Secure Technology Implementation Guides (STIGs)
- ISO 15288: Systems and Software Engineering -- System Life Cycle Processes
- ISO 27002: Information Technology -- Security Techniques -- Code of Practice for Cybersecurity Controls
- NIST 800-37: Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach
- NIST 800-39: Managing Cybersecurity Risk: Organization, Mission and Information System View
- NIST 800-53: Security and Privacy Controls for Federal Information Systems and Organizations
- NIST 800-64: Security Considerations in System Development Lifecycle
- NIST 800-122: Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
- NIST 800-160: Systems Security Engineering: Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems
- NIST 800-161: Supply Chain Risk Management Practices for Federal Information Systems and Organizations
- NIST 800-171: Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations
- NIST IR 7298: Glossary of Key Cybersecurity Terms
- NIST IR 8062: An Introduction to Privacy Engineering and Risk Management in Federal Systems
- NIST IR 8179: Criticality Analysis Process Model: Prioritizing Systems and Components [draft]
- Open Web Application Security Project (OWASP)
- OWASP Top 10 Most Critical Web Application Security Risks
- OWASP Application Security Verification Standard Project (ASVS)
- Privacy Frameworks
- Fair Information Practice Principles (FIPP)
- Generally Accepted Privacy Practices (GAPP)
- ISO 27018: Information Technology -- Security Techniques -- Code of Practice for Protection of Personally Identifiable Information (PII) in Public Clouds Acting as PII Processors
- OASIS Privacy Management Reference Model and Methodology (PMRM)
- Privacy by Design (PbD)
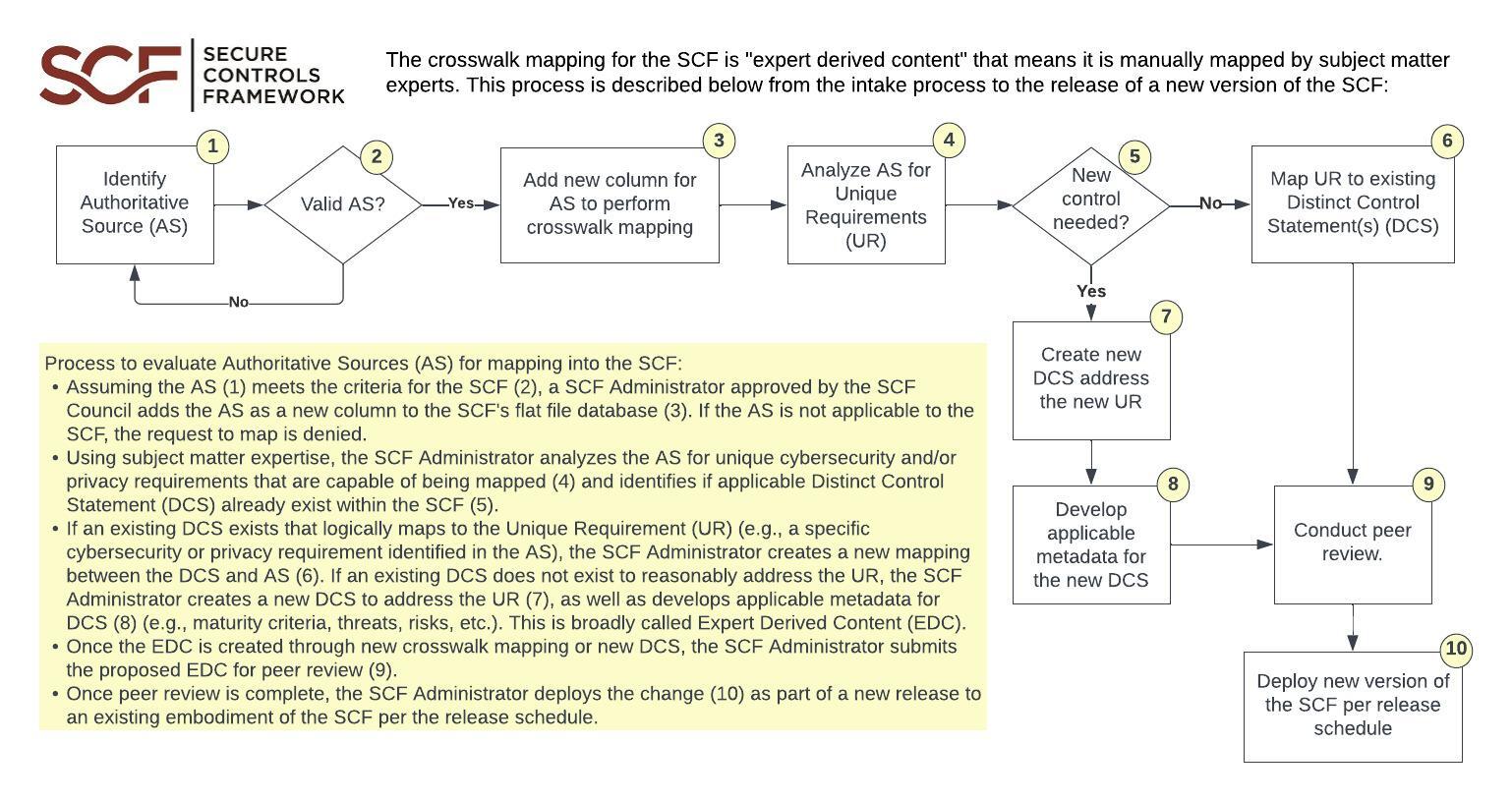
How The SCF Is Mapped
The crosswalk mapping for the SCF is "expert-derived content" which means it is manually mapped by subject matter experts. This process is described below from the intake process to the release of a new version of the SCF: