United States based kitchen utensil manufacturer OXO International disclosed a data breach that spans numerous periods over two years. This breach notification states that customer and payment information may have been exposed and further research by BleepingComputer indicates this was most likely a MageCart attack.
In a data breach notification filed with California, OXO International has stated that between June 9, 2017 – November 28, 2017, June 8, 2018 – June 9, 2018, and July 20, 2018 – October 16, 2018 their servers were compromised in order to try and steal customer's customer and payment information.
"On December 17, 2018, OXO confirmed through our forensic investigators that the security of certain personal information that you entered into our e-commerce website (https://www.oxo.com) may have been compromised," states the breach disclosure. "We currently believe that information entered in the customer order form between June 9, 2017 – November 28, 2017, June 8, 2018 – June 9, 2018, July 20, 2018 – October 16, 2018 may have been compromised. While we believe the attempt to compromise your payment information may have been ineffective, we are notifying you out of an abundance of caution."
Once they detected the compromise, they hired a third-party security firm to investigate the server and fix any vulnerabilities that were present.
For those affected, OXO is offering their customers free credit monitoring services through Kroll. In order to access this free service, you will need a member ID that will be sent to customers via the OXO notification emails.
OXO compromise was a MageCart attack
Research by BleepingComputer shows that at least one of the compromises was a MageCart attack that attempted to steal customer information.
A MageCart attack is when attackers inject an script into a site's checkout page in order to steal data, such as credit card details and addresses, that a customer inputs into the page's forms. This data is then sent to a remote site so that it can be collected by the attackers.
In a Archive.org snapshot from June 9th 2017, the source code of the checkout page shows that a JavaScript script was being loaded into the page from https://js-cloud.com/js/static.js.
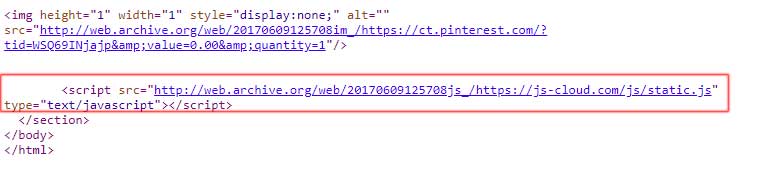
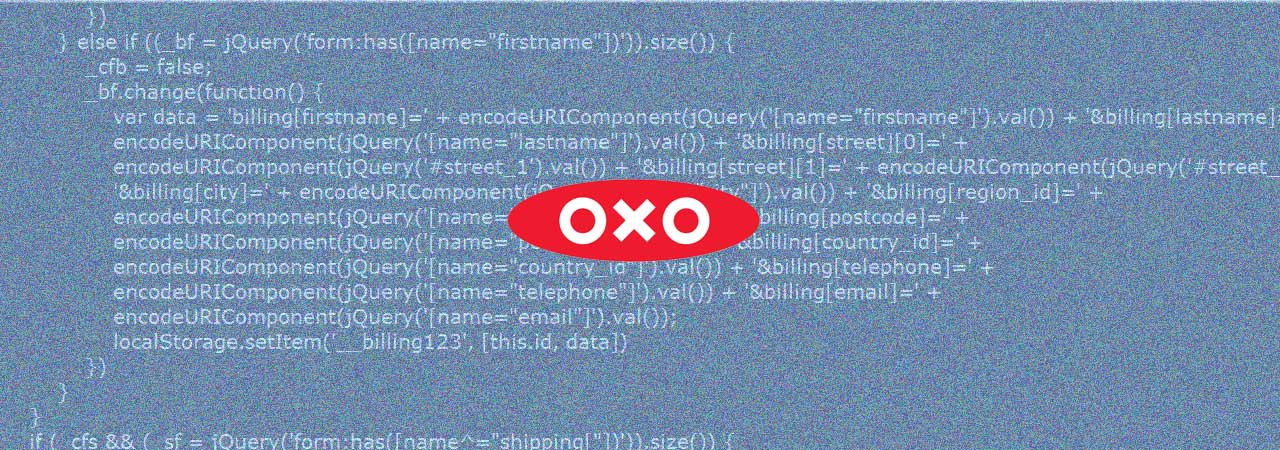
This script is no longer available, but BleepingComputer was able to find it on VirusTotal. When examining the contents of the script, it was easily seen that this is a MageCart script designed to steal payment information and contact information for an oxo.com customer.
As you can see from the two images below, the form attempted to steal credit card information and customer information such as billing addresses, email address, and telephone numbers.
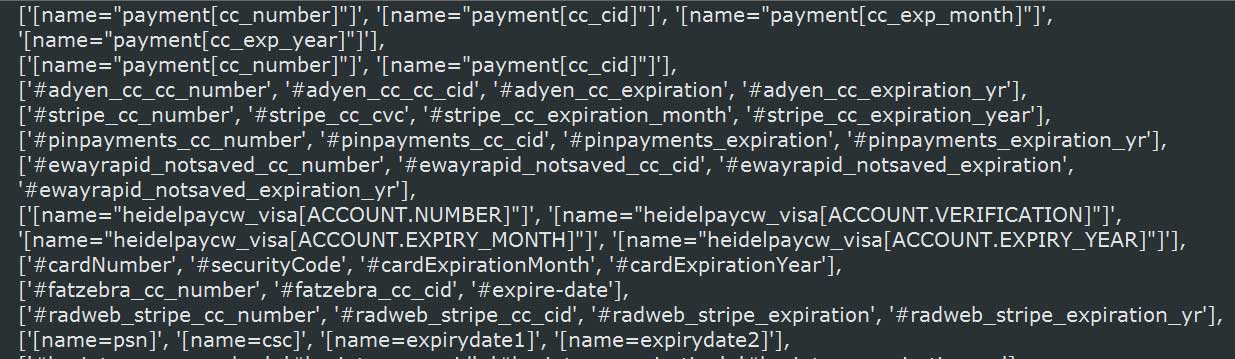

When this information was collected, it was then sent to a remote URL located at https://js-cloud.com/gate.php, which can be used by the attackers to retrieve the data.

MageCart has been a thorn in many ecommerce site's side this past year with attacks on sites belonging to British Airways, TicketMaster, Feedify, and Newegg.
With the success of these attacks, we should expect to see them continue into 2019 and beyond.
Other indications of compromise
While researching the article, BleepingComputer found another snapshot of the oxo.com site on Archive.today. This snapshot was from December 12th 2018 and the source code shows a script for the Russian https://top.mail.ru/ web site tracking service having been added to the checkout page . It is not known if the script was added to other pages on the site.

While this may have been legitimate, it would be strange for U.S. based company to be utilizing a Russian analytics service rather than a well known one like Google Analytics. This script, though, would have allowed who ever owned this stats page to learn a lot about the visitors to the oxo.com site.
BleepingComputer has contacted OXO International for further comment, but had not heard back at the time of this publication.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now