Two new reports from eSentire and Proofpoint show that that as online threats remain an issue, user security leaves much to be desired. The mismatch between the danger of cyberthreats and lack of user readiness could leave individuals or businesses at risk of serious losses to data or property. Having good security practices, such as keeping systems updated, using a variety of passwords, keeping WiFi networks secure, and running antivirus software can help ameliorate the risks.
eSentire 2018 Q2 Threat Report
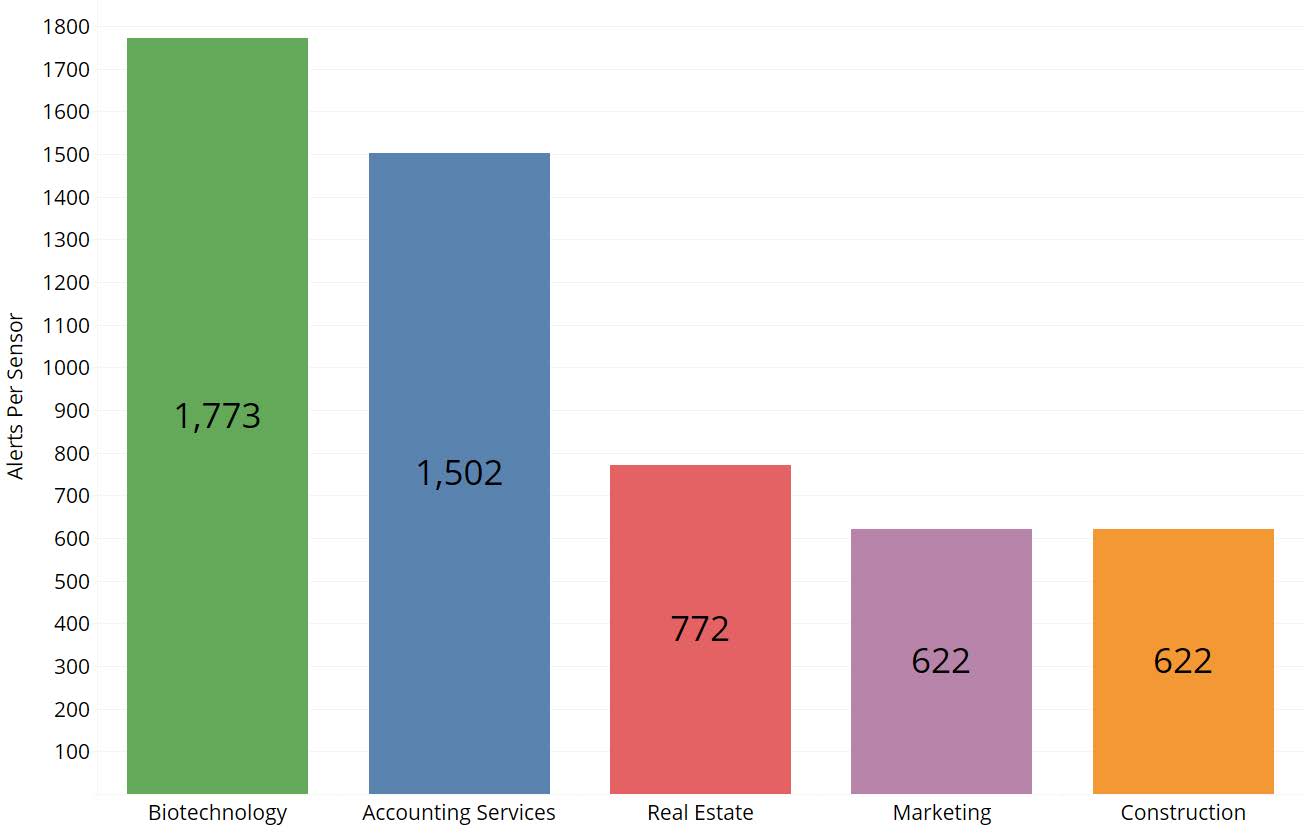
The eSentire Quarterly Threat Report looked at exploit campaigns, phishing, malware, and endpoint events throughout the second quarter of 2018. The industry most exposed to online threats was biotechnology, followed by accounting services, real estate, marketing and construction. Most attacks were looking for outdated vulnerabilities, and a small number were successful due to unpatched systems or configuration issues.
The report found a surge in Microsoft Internet Information Services (IIS) attacks, up from two thousand in the first quarter to 1.7 million in Q2, a 782x increase, largely coming from compromised servers originating from Tencent and Alibaba. Those increases continued into the third quarter.
Drupal and Oracle Web Logic were also targeted heavily by exploit attacks throughout the second quarter. The firm observed successful attacks using exploits such as Drupalgeedon2 and EternalBlue. Other devices seeing attacks included GPON home routers manufactured by DASAN Zhone Solutions, which are being targeted by botnets such as Muhstik.
In terms of malware, the Panda banking Trojan had the greatest increase quarter over quarter:
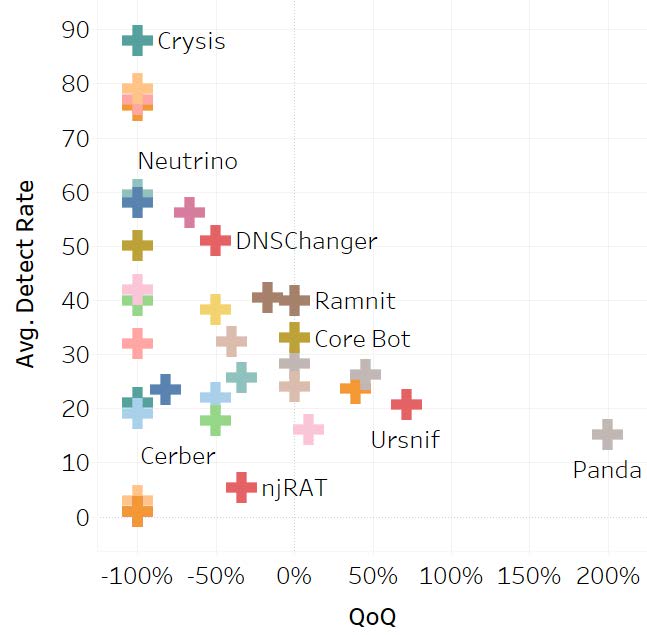
Emotet and Hancitor were also seen throughout Q2. Emotet has evolved from a banking Trojan to becoming a malware downloader which is delivered through malicious documents disguised as invoices, shipping forms and IRS tax forms. Phishing attacks also remain popular, and eSentire saw an increase in lures mimicking shipping and eFax services.
Proofpoint 2018 User Risk Report
Wombat Security, a division of Proofpoint, released a report looking at user risks in 2018. The firm commissioned a third-party survey to question 6,000 working adults in Germany, France, Italy, the U.K., the U.S., and Australia about end-user actions and capabilities that affect device, data, and system security. It tested respondents understanding of cybersecurity fundamentals that includes knowledge of phishing, ransomware and WiFi security, their password management practices, use of data protections, and social media use.
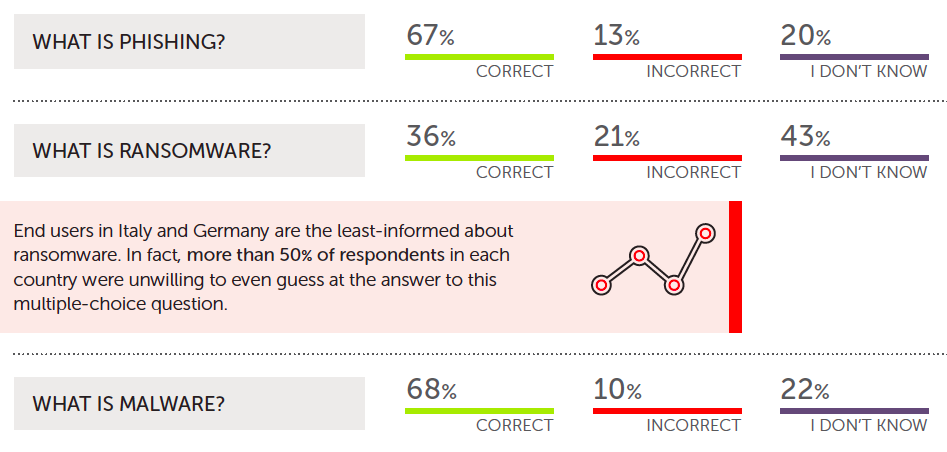
The survey found that many respondents had a limited understanding of common cybersecurity risks. More than 60 percent didn't know what ransomware was, while 32 percent didn't understand malware.
In terms of password usage, 33 percent said they used a password manager. Of those that didn't, 21 percent said they use the same one or two passwords for all their online accounts.
However, when it comes to personal cybersecurity, many respondents failed to take proper security cautions in their personal life. For firms that have employees work from home or bring their own devices, this could be an issue.
For example, 44 percent of respondents did not password-protect their home WiFi networks, and 66 percent haven’t changed the default password on their WiFi routers. Furthermore, 55 percent of respondents whose employer gives them a device to use at home allow their friends and family members the access the device.
The relatively poor security habits of many respondents might cause organizations to consider educating their employees on the risks of online threats and proper security measures to take. Wombat calls this a "people-centric" view of cybersecurity, and judging by the results of the survey, it might be a concept worth considering.


Comments
Bullwinkle-J-Moose - 5 years ago
The main problem is that different threats require a different response
For example, Linux Live with a persistence file can be a threat to Firefox.
A page may not load correctly until java scripts are enabled, But, once java scripts are enabled, Firefox can be permanently hosed by the scripts due to the persistence file
Windows 8.1 or 10 can be locked down using Shadow Mode from Shadow Defender preventing the persistence described above but Windows itself is permanently backdoored by Microsoft
I have successfully used Windows XP-SP2 without ANY Microsoft security updates and an antivirus that expired in 2015 to study online malware threats
I have not found ANY persistent threat that can destroy this XP install and have had absolutely ZERO Blue screens of death in over 10 years now
Passwords are never used on the XP Box
Online banking is a no-no and no sensitive information is ever kept on the drive
but...
After studying a malware sample, a simple reboot wipes the malware and I'm back to a clean install of Windows XP
How?
Driveshield locks the install as READ ONLY!
No Java scripts allowed
No Net Framework allowed
No Flash allowed
No Silverlight allowed
Aftermarket firewall
ALL Microsoft components are blocked from Internet access
SMB1 disabled
vulnerable ports blocked
and many many other tweaks
It may not be good for online banking (what is at this point?) but it's Rock Solid, reliable and indestructible with ME disabled and a Read Only Copy of my password protected BIOS
Oh, and the backup is on Optical Read Only media
ALL online threats cannot be stopped by a single O.S.
Different threats require different protections
Too bad Microsoft is now the major threat!